 解决-进一步分析与改造[二]
解决-进一步分析与改造[二]
# 1. JVM 配置调整与失效分析
面对 SecureRandom 卡死,许多用户第一反应是直接修改 JVM 配置,试图让 Java 使用非阻塞的 /dev/urandom。常见做法如下:
- 在 java.security 配置中将
securerandom.source=file:/dev/random替换为securerandom.source=file:/dev/urandom
配置样例(实际路径以本机为准):
[root@hadoop1 security]# cat java.security
security.provider.1=SUN
security.provider.2=SunRsaSign
security.provider.3=SunEC
security.provider.4=SunJSSE
security.provider.5=SunJCE
security.provider.6=SunJGSS
security.provider.7=SunSASL
security.provider.8=XMLDSig
security.provider.9=SunPCSC
security.provider.10=JdkLDAP
security.provider.11=JdkSASL
security.provider.12=SunPKCS11
securerandom.source=file:/dev/urandom
securerandom.strongAlgorithms=NativePRNGBlocking:SUN,DRBG:SUN
securerandom.drbg.config=
login.configuration.provider=sun.security.provider.ConfigFile
policy.provider=sun.security.provider.PolicyFile
policy.url.1=file:${java.home}/conf/security/java.policy
policy.url.2=file:${user.home}/.java.policy
policy.expandProperties=true
policy.allowSystemProperty=true
policy.ignoreIdentityScope=false
keystore.type=pkcs12
keystore.type.compat=true
package.access=sun.misc.,\
sun.reflect.
package.definition=sun.misc.,\
sun.reflect.
security.overridePropertiesFile=true
ssl.KeyManagerFactory.algorithm=SunX509
ssl.TrustManagerFactory.algorithm=PKIX
networkaddress.cache.negative.ttl=10
krb5.kdc.bad.policy = tryLast
sun.security.krb5.disableReferrals=false
sun.security.krb5.maxReferrals=5
jdk.certpath.disabledAlgorithms=MD2, MD5, SHA1 jdkCA & usage TLSServer, \
RSA keySize < 1024, DSA keySize < 1024, EC keySize < 224, \
SHA1 usage SignedJAR & denyAfter 2019-01-01
jdk.security.legacyAlgorithms=SHA1, \
RSA keySize < 2048, DSA keySize < 2048
jdk.jar.disabledAlgorithms=MD2, MD5, RSA keySize < 1024, \
DSA keySize < 1024, SHA1 denyAfter 2019-01-01
jdk.tls.disabledAlgorithms=SSLv3, TLSv1, TLSv1.1, DTLSv1.0, RC4, DES, \
MD5withRSA, DH keySize < 1024, EC keySize < 224, 3DES_EDE_CBC, anon, NULL, \
ECDH
jdk.tls.legacyAlgorithms=NULL, anon, RC4, DES, 3DES_EDE_CBC
jdk.tls.keyLimits=AES/GCM/NoPadding KeyUpdate 2^37, \
ChaCha20-Poly1305 KeyUpdate 2^37
crypto.policy=unlimited
jdk.xml.dsig.secureValidationPolicy=\
disallowAlg http://www.w3.org/TR/1999/REC-xslt-19991116,\
disallowAlg http://www.w3.org/2001/04/xmldsig-more#rsa-md5,\
disallowAlg http://www.w3.org/2001/04/xmldsig-more#hmac-md5,\
disallowAlg http://www.w3.org/2001/04/xmldsig-more#md5,\
disallowAlg http://www.w3.org/2000/09/xmldsig#sha1,\
disallowAlg http://www.w3.org/2000/09/xmldsig#dsa-sha1,\
disallowAlg http://www.w3.org/2000/09/xmldsig#rsa-sha1,\
disallowAlg http://www.w3.org/2007/05/xmldsig-more#sha1-rsa-MGF1,\
disallowAlg http://www.w3.org/2001/04/xmldsig-more#ecdsa-sha1,\
maxTransforms 5,\
maxReferences 30,\
disallowReferenceUriSchemes file http https,\
minKeySize RSA 1024,\
minKeySize DSA 1024,\
minKeySize EC 224,\
noDuplicateIds,\
noRetrievalMethodLoops
jceks.key.serialFilter = java.base/java.lang.Enum;java.base/java.security.KeyRep;\
java.base/java.security.KeyRep$Type;java.base/javax.crypto.spec.SecretKeySpec;!*
jdk.sasl.disabledMechanisms=
jdk.security.caDistrustPolicies=SYMANTEC_TLS,ENTRUST_TLS,CAMERFIRMA_TLS
jdk.io.permissionsUseCanonicalPath=false
jdk.tls.alpnCharset=ISO_8859_1
[root@hadoop1 security]# pwd
/opt/modules/jdk-17.0.15+6/conf/security
[root@hadoop1 security]#
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
提示
无论通过 JAVA 参数(如 -Djava.security.egd=file:/dev/urandom),还是直接编辑配置文件,这类手段都意图让 SecureRandom 使用非阻塞熵源,理论上可规避卡死。
但在 Temurin 17 / AdoptOpenJDK 17 上实测均无效。查阅官方和社区资料后可以确认: 行业通病
即使改成 /dev/urandom,JVM 依然优先从 /dev/random 读取(详见前文问题归因分析)。此时 Ambari 启动卡死问题依旧反复出现。
# 2. 推荐方案:直接安装熵池加速器
既然配置绕不过 JDK 层逻辑,那最根本的做法就是——提高操作系统的熵池生成速度,让 SecureRandom 能尽快获取足够熵值。
提示
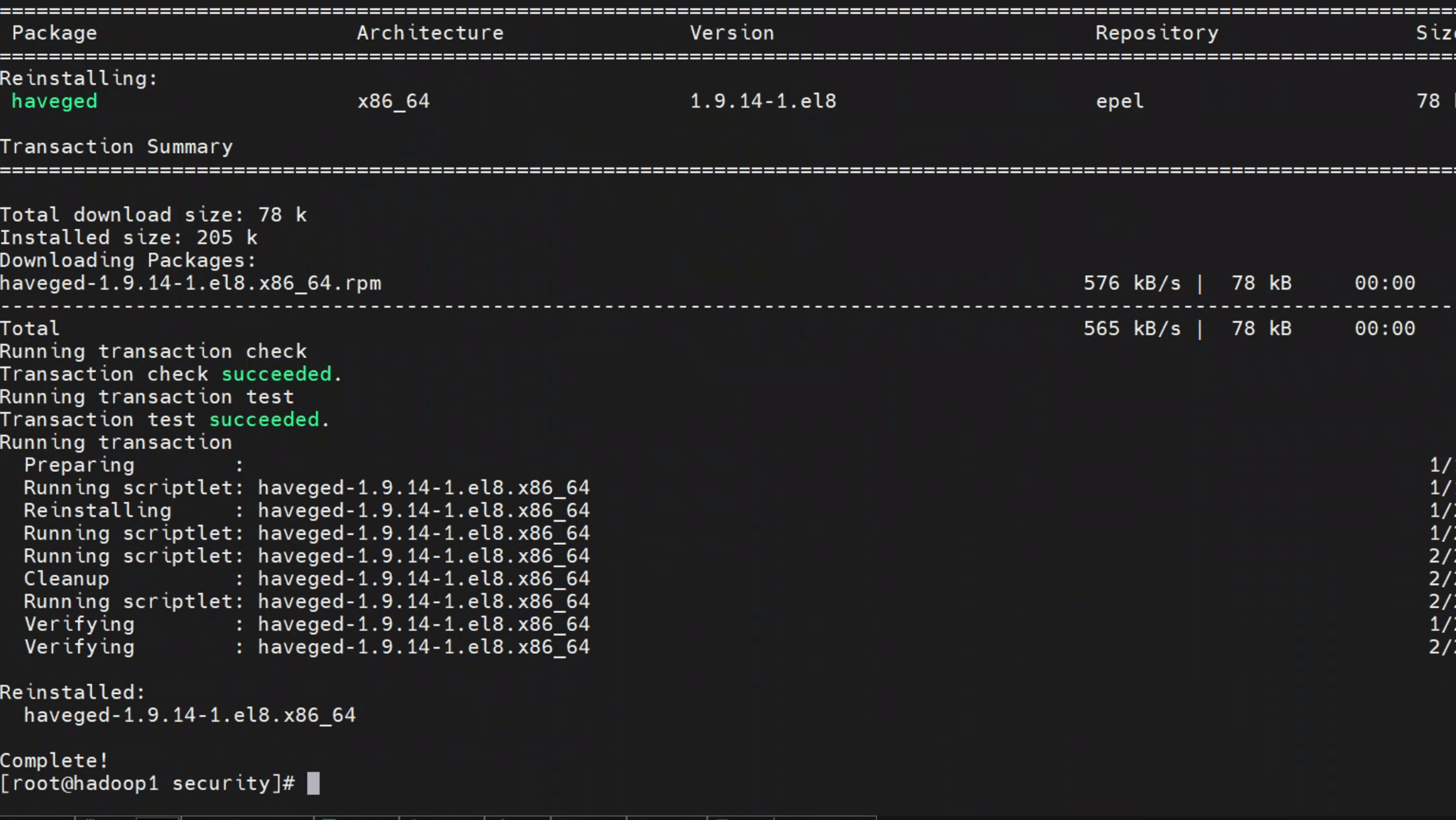
Rocky Linux/CentOS 8 建议使用 haveged 工具,高效生成系统熵,彻底解除 JVM 低熵瓶颈。
安装与激活只需三步:
dnf install haveged -y
systemctl enable haveged --now
systemctl status haveged
1
2
3
2
3
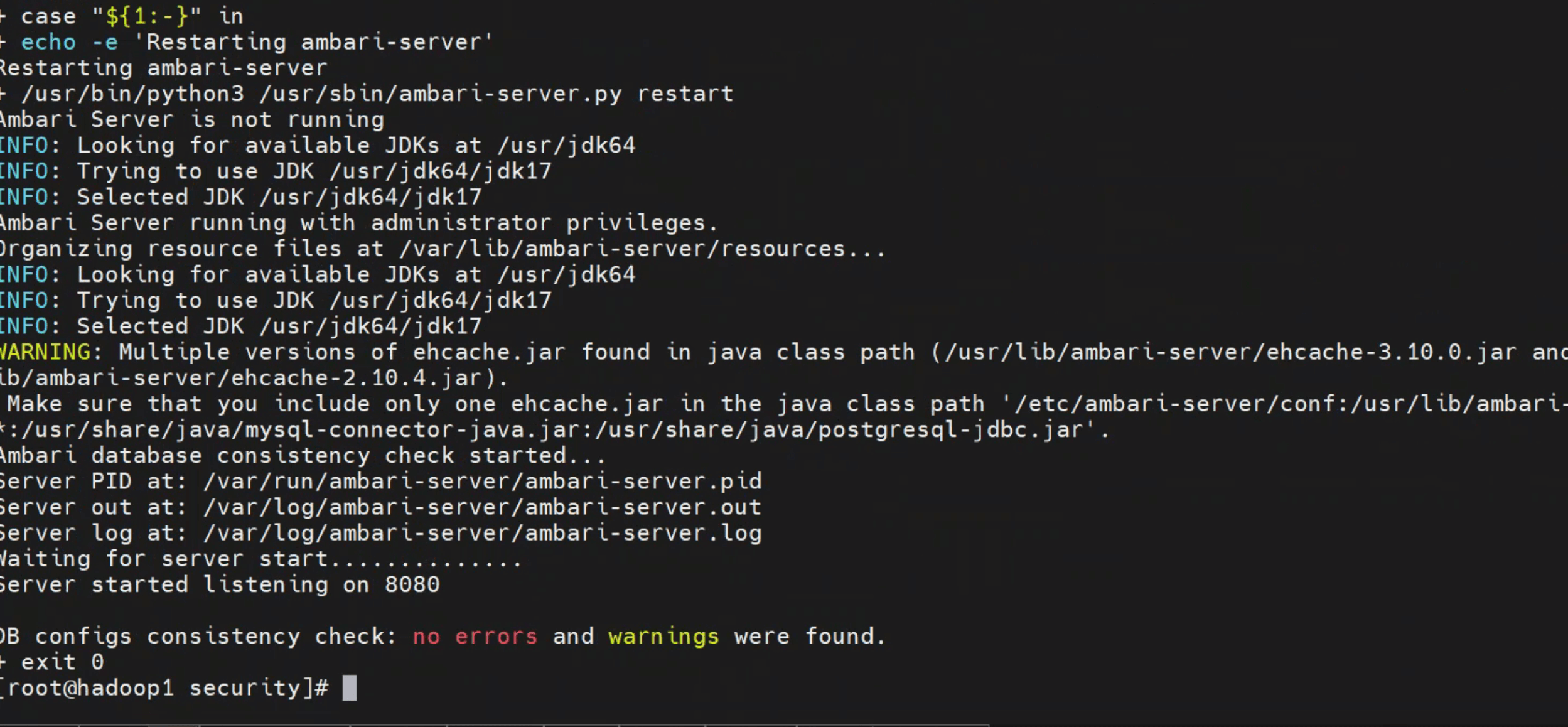
# 3. 启动前后熵池变化对比
启用 haveged 后,通过如下命令可观察到熵池数值迅速提升:
cat /proc/sys/kernel/random/entropy_avail
1
如图所示,启动前系统熵池数值常常低于 200,极易触发卡死。haveged 启用后,熵值立刻提升至 3000+,Ambari/JVM 启动流畅无阻。实测效果
- 03
- Ranger Admin 证书快速导入脚本02-15
