 Ranger Admin LDAP 认证报 Bad credentials 分析
Ranger Admin LDAP 认证报 Bad credentials 分析
需要 ttr-release 版本 >= 2.2.3
- Ambari 3.0.0 + FreeIPA 统一认证体系
- 示例环境:Kylin V10 SP3 x86
- Realm:TEST.COM
# 一、问题现象与排查入口
Ranger Admin 对接 FreeIPA/LDAP 后,常见现象是页面提示 Bad credentials。 这类问题优先不要从“密码对不对”入手,而是先把日志打出来:DN 是怎么拼出来的、search 是在哪个 base 下做的,基本一眼就能确定根因。
关键思路
- 看到
Failed to bind with any user DNs [...]:优先怀疑 dnpattern 拼错 DN - 看到
error code 32 - No Such Object/remaining name 'dc=example,dc=com':优先怀疑 Base DN / SearchBase 仍然是默认值或残留错误
# 二、日志解读:用两句关键行锁定根因
# 1、第一类:dnpattern 拼错 DN(Bind 直接失败)
日志里最关键的一句:
DEBUG [BindAuthenticator.java:80] Failed to bind with any user DNs [uid=admin,ou=users,dc=xasecure,dc=net]
这句出现就别纠结密码
Failed to bind with any user DNs [...] 的含义非常明确:
Ranger 已经构造出了候选 userDN(通常来自 ranger.ldap.user.dnpattern),但这些 DN 绑定全部失败。
在 FreeIPA 场景中,最常见就是 dnpattern 把 DN 写死到了错误的目录树。
# 2、第二类:Base DN / SearchBase 错(Search 找不到对象)
同一段日志里还有另一类典型错误:
InternalAuthenticationServiceException: [LDAP: error code 32 - No Such Object]
... remaining name 'dc=example,dc=com'
2
这句基本等价于“目录根写错了”
error code 32 - No Such Object 表示 Ranger 在指定的 rootDN/searchBase 下做 search,但 LDAP 目录里压根不存在这个 DN。
这里出现 dc=example,dc=com,非常典型:默认模板没清干净 / Base DN 沿用了示例值。
# 3、原始日志
2026-02-10 10:40:35,956 [http-nio-6080-exec-3] DEBUG [HttpSessionSecurityContextRepository.java:189] Retrieved SecurityContextImpl [Authentication=UsernamePasswordAuthenticationToken [Principal=org.springframework.security.core.userdetails.User [Username=rangerusersync, Password=[PROTECTED], Enabled=true, AccountNonExpired=true, credentialsNonExpired=true, AccountNonLocked=true, Granted Authorities=[ROLE_SYS_ADMIN]], Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=192.168.3.236, SessionId=C7BA391D57C2828662F4BAE45E489ABA], Granted Authorities=[ROLE_SYS_ADMIN]]]
2026-02-10 10:40:35,956 [http-nio-6080-exec-3] DEBUG [SecurityContextPersistenceFilter.java:109] Set SecurityContextHolder to SecurityContextImpl [Authentication=UsernamePasswordAuthenticationToken [Principal=org.springframework.security.core.userdetails.User [Username=rangerusersync, Password=[PROTECTED], Enabled=true, AccountNonExpired=true, credentialsNonExpired=true, AccountNonLocked=true, Granted Authorities=[ROLE_SYS_ADMIN]], Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=192.168.3.236, SessionId=C7BA391D57C2828662F4BAE45E489ABA], Granted Authorities=[ROLE_SYS_ADMIN]]]
2026-02-10 10:40:35,956 [http-nio-6080-exec-3] DEBUG [RangerKRBAuthenticationFilter.java:368] RangerKRBAuthenticationFilter: request URL = /service/xusers/users/roleassignments
2026-02-10 10:40:35,957 [http-nio-6080-exec-3] DEBUG [RangerCSRFPreventionFilter.java:170] actualCsrfToken = null clientCsrfToken = nulltrustedProxy = false for /service/xusers/users/roleassignments
2026-02-10 10:40:35,957 [http-nio-6080-exec-3] DEBUG [AbstractSecurityInterceptor.java:210] Authorized filter invocation [POST /service/xusers/users/roleassignments] with attributes [isAuthenticated()]
2026-02-10 10:40:35,958 [http-nio-6080-exec-3] DEBUG [FilterChainProxy.java:333] Secured POST /service/xusers/users/roleassignments
2026-02-10 10:40:35,982 [http-nio-6080-exec-3] DEBUG [AbstractSecurityInterceptor.java:210] Authorized ReflectiveMethodInvocation: public java.util.List org.apache.ranger.rest.XUserREST.setXUserRolesByName(org.apache.ranger.ugsyncutil.model.UsersGroupRoleAssignments); target is of class [org.apache.ranger.rest.XUserREST] with attributes [[authorize: 'hasRole('ROLE_SYS_ADMIN')', filter: 'null', filterTarget: 'null']]
2026-02-10 10:40:35,983 [http-nio-6080-exec-3] DEBUG [XUserMgr.java:2837] Request users for role updates = [keyadmin, admin, rangerusersync, rangertagsync]
2026-02-10 10:40:36,002 [http-nio-6080-exec-3] INFO [XUserMgr.java:2848] keyadmin is internal to ranger admin and hence ignoring role assignments
2026-02-10 10:40:36,011 [http-nio-6080-exec-3] INFO [XUserMgr.java:2848] admin is internal to ranger admin and hence ignoring role assignments
2026-02-10 10:40:36,018 [http-nio-6080-exec-3] INFO [XUserMgr.java:2848] rangerusersync is internal to ranger admin and hence ignoring role assignments
2026-02-10 10:40:36,026 [http-nio-6080-exec-3] INFO [XUserMgr.java:2848] rangertagsync is internal to ranger admin and hence ignoring role assignments
2026-02-10 10:40:36,030 [http-nio-6080-exec-3] DEBUG [XUserMgr.java:2904] Existing non user role users = []
2026-02-10 10:40:36,033 [http-nio-6080-exec-3] DEBUG [SecurityContextPersistenceFilter.java:120] Cleared SecurityContextHolder to complete request
2026-02-10 10:40:36,055 [http-nio-6080-exec-4] DEBUG [FilterChainProxy.java:218] Securing POST /service/xusers/ugsync/auditinfo/
2026-02-10 10:40:36,055 [http-nio-6080-exec-4] DEBUG [HttpSessionSecurityContextRepository.java:189] Retrieved SecurityContextImpl [Authentication=UsernamePasswordAuthenticationToken [Principal=org.springframework.security.core.userdetails.User [Username=rangerusersync, Password=[PROTECTED], Enabled=true, AccountNonExpired=true, credentialsNonExpired=true, AccountNonLocked=true, Granted Authorities=[ROLE_SYS_ADMIN]], Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=192.168.3.236, SessionId=C7BA391D57C2828662F4BAE45E489ABA], Granted Authorities=[ROLE_SYS_ADMIN]]]
2026-02-10 10:40:36,055 [http-nio-6080-exec-4] DEBUG [SecurityContextPersistenceFilter.java:109] Set SecurityContextHolder to SecurityContextImpl [Authentication=UsernamePasswordAuthenticationToken [Principal=org.springframework.security.core.userdetails.User [Username=rangerusersync, Password=[PROTECTED], Enabled=true, AccountNonExpired=true, credentialsNonExpired=true, AccountNonLocked=true, Granted Authorities=[ROLE_SYS_ADMIN]], Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=192.168.3.236, SessionId=C7BA391D57C2828662F4BAE45E489ABA], Granted Authorities=[ROLE_SYS_ADMIN]]]
2026-02-10 10:40:36,056 [http-nio-6080-exec-4] DEBUG [RangerKRBAuthenticationFilter.java:368] RangerKRBAuthenticationFilter: request URL = /service/xusers/ugsync/auditinfo/
2026-02-10 10:40:36,056 [http-nio-6080-exec-4] DEBUG [RangerCSRFPreventionFilter.java:170] actualCsrfToken = null clientCsrfToken = nulltrustedProxy = false for /service/xusers/ugsync/auditinfo/
2026-02-10 10:40:36,057 [http-nio-6080-exec-4] DEBUG [AbstractSecurityInterceptor.java:210] Authorized filter invocation [POST /service/xusers/ugsync/auditinfo/] with attributes [isAuthenticated()]
2026-02-10 10:40:36,058 [http-nio-6080-exec-4] DEBUG [FilterChainProxy.java:333] Secured POST /service/xusers/ugsync/auditinfo/
2026-02-10 10:40:36,080 [http-nio-6080-exec-4] DEBUG [AbstractSecurityInterceptor.java:210] Authorized ReflectiveMethodInvocation: public org.apache.ranger.view.VXUgsyncAuditInfo org.apache.ranger.rest.XUserREST.postUserGroupAuditInfo(org.apache.ranger.view.VXUgsyncAuditInfo); target is of class [org.apache.ranger.rest.XUserREST] with attributes [[authorize: 'hasRole('ROLE_SYS_ADMIN')', filter: 'null', filterTarget: 'null']]
2026-02-10 10:40:36,103 [http-nio-6080-exec-4] DEBUG [SecurityContextPersistenceFilter.java:120] Cleared SecurityContextHolder to complete request
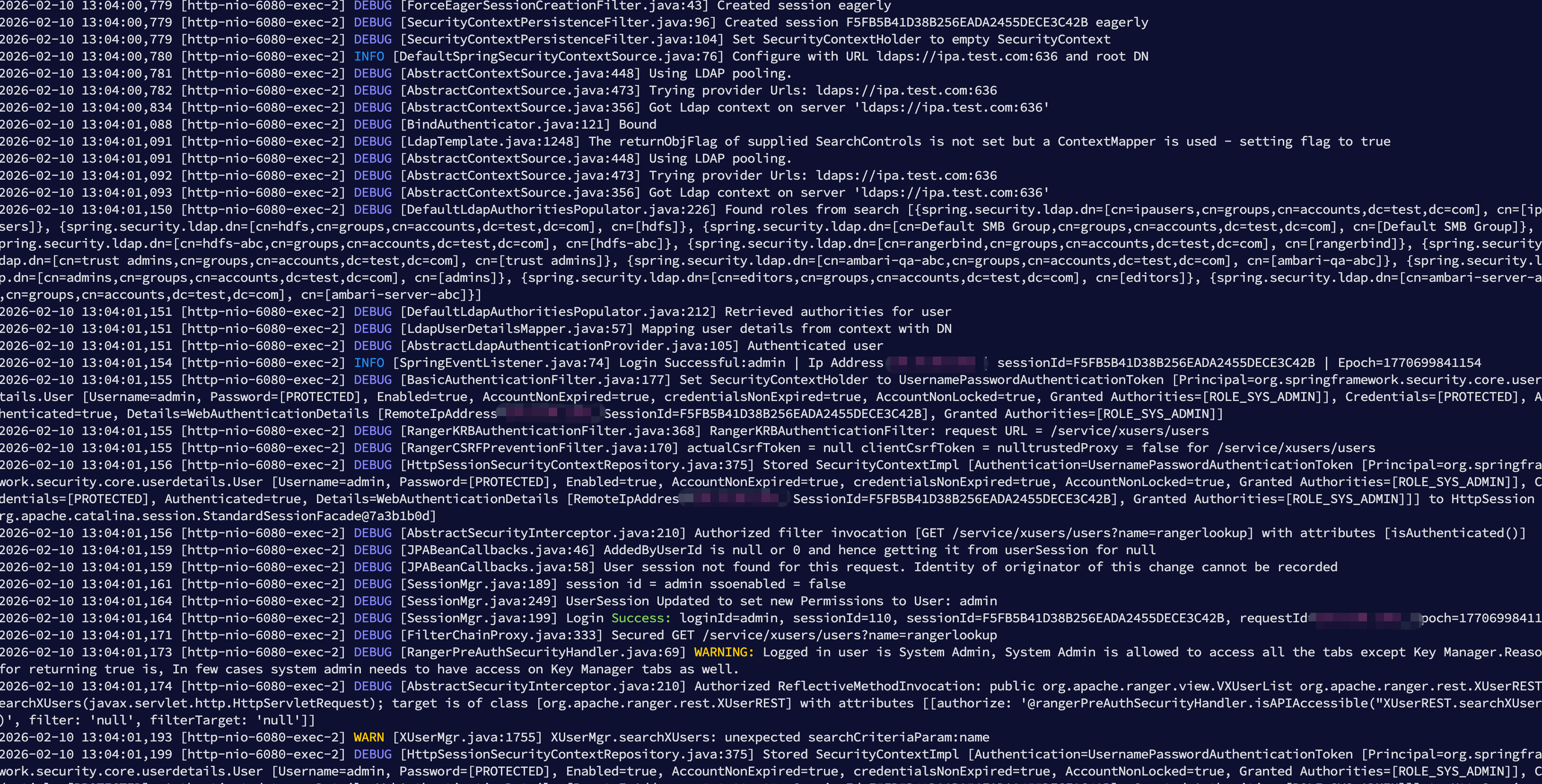
2026-02-10 10:40:47,110 [http-nio-6080-exec-10] DEBUG [FilterChainProxy.java:218] Securing GET /service/xusers/users?name=rangerlookup
2026-02-10 10:40:47,110 [http-nio-6080-exec-10] DEBUG [ForceEagerSessionCreationFilter.java:43] Created session eagerly
2026-02-10 10:40:47,111 [http-nio-6080-exec-10] DEBUG [SecurityContextPersistenceFilter.java:96] Created session 1C455207DE1D6ACC6F4716121B17F172 eagerly
2026-02-10 10:40:47,111 [http-nio-6080-exec-10] DEBUG [SecurityContextPersistenceFilter.java:104] Set SecurityContextHolder to empty SecurityContext
2026-02-10 10:40:47,146 [http-nio-6080-exec-10] INFO [DefaultSpringSecurityContextSource.java:76] Configure with URL ldaps://ipa.test.com:636 and root DN
2026-02-10 10:40:47,197 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:448] Using LDAP pooling.
2026-02-10 10:40:47,198 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:473] Trying provider Urls: ldaps://ipa.test.com:636
2026-02-10 10:40:47,310 [http-nio-6080-exec-10] DEBUG [BindAuthenticator.java:80] Failed to bind with any user DNs [uid=admin,ou=users,dc=xasecure,dc=net]
2026-02-10 10:40:47,325 [http-nio-6080-exec-10] DEBUG [RangerAuthenticationProvider.java:291] LDAP Authentication Failed:
org.springframework.security.authentication.BadCredentialsException: Bad credentials
at org.springframework.security.ldap.authentication.BindAuthenticator.authenticate(BindAuthenticator.java:94)
at org.springframework.security.ldap.authentication.LdapAuthenticationProvider.doAuthentication(LdapAuthenticationProvider.java:174)
at org.springframework.security.ldap.authentication.AbstractLdapAuthenticationProvider.authenticate(AbstractLdapAuthenticationProvider.java:79)
at org.apache.ranger.security.handler.RangerAuthenticationProvider.getLdapAuthentication(RangerAuthenticationProvider.java:284)
at org.apache.ranger.security.handler.RangerAuthenticationProvider.authenticate(RangerAuthenticationProvider.java:116)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:182)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:201)
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:172)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:223)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:217)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.authentication.logout.LogoutFilter.doFilter(LogoutFilter.java:103)
at org.springframework.security.web.authentication.logout.LogoutFilter.doFilter(LogoutFilter.java:89)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:90)
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:75)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:55)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:112)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.session.ForceEagerSessionCreationFilter.doFilterInternal(ForceEagerSessionCreationFilter.java:45)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.session.DisableEncodeUrlFilter.doFilterInternal(DisableEncodeUrlFilter.java:42)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:221)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:354)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:267)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:181)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:156)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:167)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:90)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:494)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:130)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:93)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:682)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:367)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:639)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:63)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:932)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1695)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1191)
at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.lang.Thread.run(Thread.java:748)
2026-02-10 10:40:47,326 [http-nio-6080-exec-10] INFO [DefaultSpringSecurityContextSource.java:76] Configure with URL ldaps://ipa.test.com:636 and root DN
2026-02-10 10:40:47,326 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:423] AuthenticationSource not set - using default implementation
2026-02-10 10:40:47,330 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:448] Using LDAP pooling.
2026-02-10 10:40:47,330 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:473] Trying provider Urls: ldaps://ipa.test.com:636
2026-02-10 10:40:47,386 [http-nio-6080-exec-10] DEBUG [BindAuthenticator.java:80] Failed to bind with any user DNs [uid=admin,ou=users,dc=xasecure,dc=net]
2026-02-10 10:40:47,388 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:448] Using LDAP pooling.
2026-02-10 10:40:47,388 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:473] Trying provider Urls: ldaps://ipa.test.com:636
2026-02-10 10:40:47,662 [http-nio-6080-exec-10] DEBUG [AbstractContextSource.java:356] Got Ldap context on server 'ldaps://ipa.test.com:636'
2026-02-10 10:40:47,669 [http-nio-6080-exec-10] DEBUG [RangerAuthenticationProvider.java:598] LDAP Authentication Failed:
org.springframework.security.authentication.InternalAuthenticationServiceException: [LDAP: error code 32 - No Such Object]; nested exception is javax.naming.NameNotFoundException: [LDAP: error code 32 - No Such Object]; remaining name 'dc=example,dc=com'
at org.springframework.security.ldap.authentication.LdapAuthenticationProvider.doAuthentication(LdapAuthenticationProvider.java:190)
at org.springframework.security.ldap.authentication.AbstractLdapAuthenticationProvider.authenticate(AbstractLdapAuthenticationProvider.java:79)
at org.apache.ranger.security.handler.RangerAuthenticationProvider.getLdapBindAuthentication(RangerAuthenticationProvider.java:591)
at org.apache.ranger.security.handler.RangerAuthenticationProvider.authenticate(RangerAuthenticationProvider.java:120)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:182)
at org.springframework.security.authentication.ProviderManager.authenticate(ProviderManager.java:201)
at org.springframework.security.web.authentication.www.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:172)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:223)
at org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter.doFilter(AbstractAuthenticationProcessingFilter.java:217)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.authentication.logout.LogoutFilter.doFilter(LogoutFilter.java:103)
at org.springframework.security.web.authentication.logout.LogoutFilter.doFilter(LogoutFilter.java:89)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.header.HeaderWriterFilter.doHeadersAfter(HeaderWriterFilter.java:90)
at org.springframework.security.web.header.HeaderWriterFilter.doFilterInternal(HeaderWriterFilter.java:75)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.context.request.async.WebAsyncManagerIntegrationFilter.doFilterInternal(WebAsyncManagerIntegrationFilter.java:55)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:112)
at org.springframework.security.web.context.SecurityContextPersistenceFilter.doFilter(SecurityContextPersistenceFilter.java:82)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.session.ForceEagerSessionCreationFilter.doFilterInternal(ForceEagerSessionCreationFilter.java:45)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.session.DisableEncodeUrlFilter.doFilterInternal(DisableEncodeUrlFilter.java:42)
at org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:117)
at org.springframework.security.web.FilterChainProxy$VirtualFilterChain.doFilter(FilterChainProxy.java:346)
at org.springframework.security.web.FilterChainProxy.doFilterInternal(FilterChainProxy.java:221)
at org.springframework.security.web.FilterChainProxy.doFilter(FilterChainProxy.java:186)
at org.springframework.web.filter.DelegatingFilterProxy.invokeDelegate(DelegatingFilterProxy.java:354)
at org.springframework.web.filter.DelegatingFilterProxy.doFilter(DelegatingFilterProxy.java:267)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:181)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:156)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:167)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:90)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:494)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:130)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:93)
at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:682)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:74)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:367)
at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:639)
at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:63)
at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:932)
at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1695)
at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49)
at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1191)
at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.lang.Thread.run(Thread.java:748)
Caused by: org.springframework.ldap.NameNotFoundException: [LDAP: error code 32 - No Such Object]; nested exception is javax.naming.NameNotFoundException: [LDAP: error code 32 - No Such Object]; remaining name 'dc=example,dc=com'
at org.springframework.ldap.support.LdapUtils.convertLdapException(LdapUtils.java:183)
at org.springframework.ldap.core.LdapTemplate.executeWithContext(LdapTemplate.java:824)
at org.springframework.ldap.core.LdapTemplate.executeReadOnly(LdapTemplate.java:807)
at org.springframework.security.ldap.SpringSecurityLdapTemplate.searchForSingleEntry(SpringSecurityLdapTemplate.java:260)
at org.springframework.security.ldap.search.FilterBasedLdapUserSearch.searchForUser(FilterBasedLdapUserSearch.java:100)
at org.springframework.security.ldap.authentication.BindAuthenticator.authenticate(BindAuthenticator.java:86)
at org.springframework.security.ldap.authentication.LdapAuthenticationProvider.doAuthentication(LdapAuthenticationProvider.java:174)
... 53 common frames omitted
Caused by: javax.naming.NameNotFoundException: [LDAP: error code 32 - No Such Object]
at com.sun.jndi.ldap.LdapCtx.mapErrorCode(LdapCtx.java:3179)
at com.sun.jndi.ldap.LdapCtx.processReturnCode(LdapCtx.java:3100)
at com.sun.jndi.ldap.LdapCtx.processReturnCode(LdapCtx.java:2891)
at com.sun.jndi.ldap.LdapCtx.searchAux(LdapCtx.java:1846)
at com.sun.jndi.ldap.LdapCtx.c_search(LdapCtx.java:1769)
at com.sun.jndi.ldap.LdapCtx.c_search(LdapCtx.java:1786)
at com.sun.jndi.toolkit.ctx.ComponentDirContext.p_search(ComponentDirContext.java:418)
at com.sun.jndi.toolkit.ctx.PartialCompositeDirContext.search(PartialCompositeDirContext.java:396)
at javax.naming.directory.InitialDirContext.search(InitialDirContext.java:297)
at org.springframework.security.ldap.SpringSecurityLdapTemplate.searchForSingleEntryInternal(SpringSecurityLdapTemplate.java:271)
at org.springframework.security.ldap.SpringSecurityLdapTemplate.lambda$searchForSingleEntry$3(SpringSecurityLdapTemplate.java:260)
at org.springframework.ldap.core.LdapTemplate.executeWithContext(LdapTemplate.java:821)
... 58 common frames omitted
2026-02-10 10:40:47,721 [http-nio-6080-exec-10] DEBUG [AbstractUserDetailsAuthenticationProvider.java:199] Authenticated user
2026-02-10 10:40:47,722 [http-nio-6080-exec-10] INFO [SpringEventListener.java:74] Login Successful:admin | Ip Address:192.168.3.235 | sessionId=1C455207DE1D6ACC6F4716121B17F172 | Epoch=1770691247722
2026-02-10 10:40:47,723 [http-nio-6080-exec-10] DEBUG [BasicAuthenticationFilter.java:177] Set SecurityContextHolder to UsernamePasswordAuthenticationToken [Principal=org.springframework.security.core.userdetails.User [Username=admin, Password=[PROTECTED], Enabled=true, AccountNonExpired=true, credentialsNonExpired=true, AccountNonLocked=true, Granted Authorities=[ROLE_SYS_ADMIN]], Credentials=[PROTECTED], Authenticated=true, Details=WebAu
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
# 三、配置修复:Base DN 与 User SearchBase 必须改对
# 1、LDAP Base DN:默认值必须改掉
首先第一个:LDAP base dn 要设置对,默认是需要修改的。
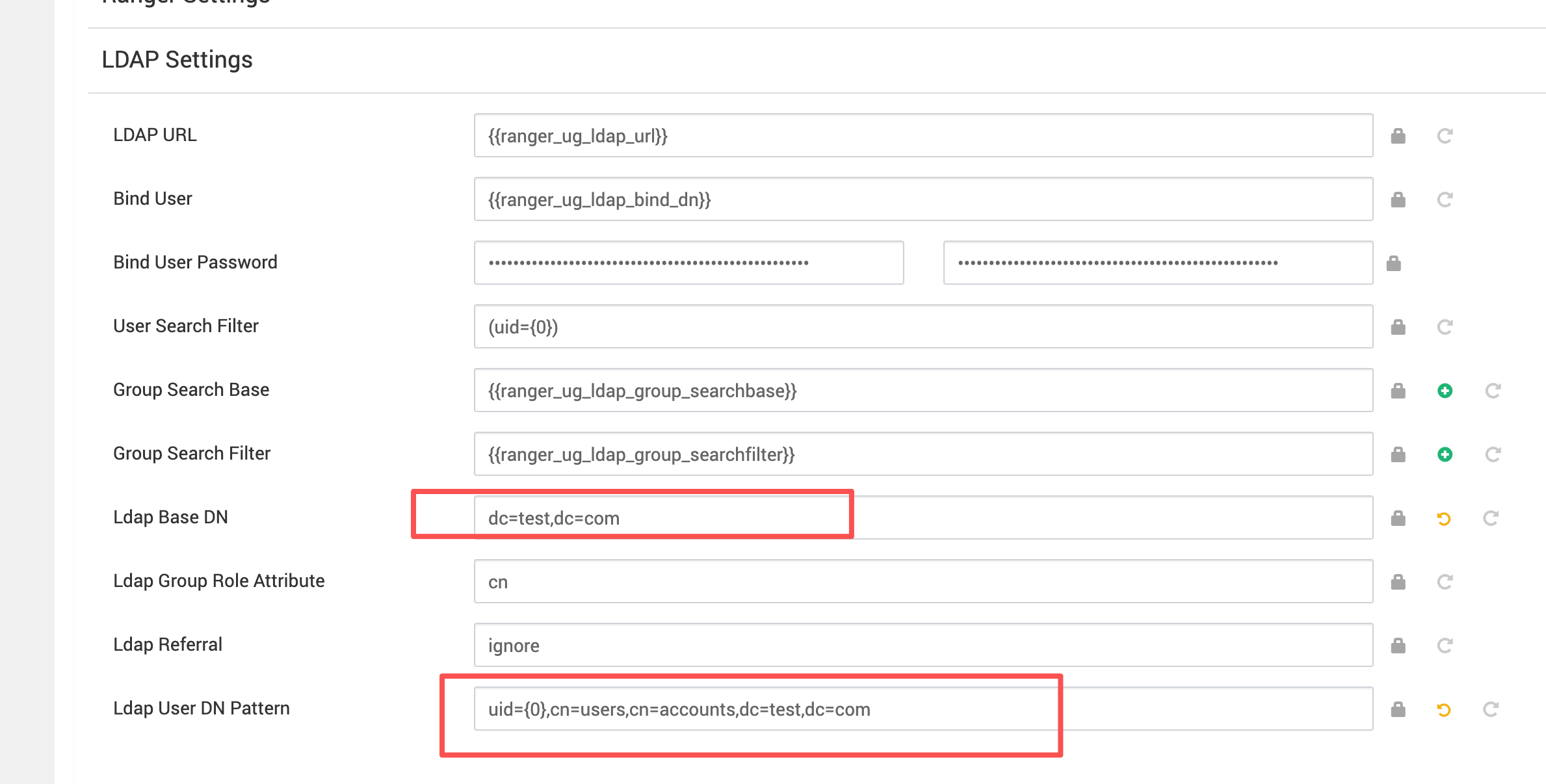
推荐值(按本文示例环境)
dc=test,dc=com
# 2、ranger.ldap.user.searchbase:用户搜索根必须覆盖真实用户 DN
其次是 Ranger 这块:ranger.ldap.user.searchbase 也要设置对。
cn=users,cn=accounts,dc=test,dc=com
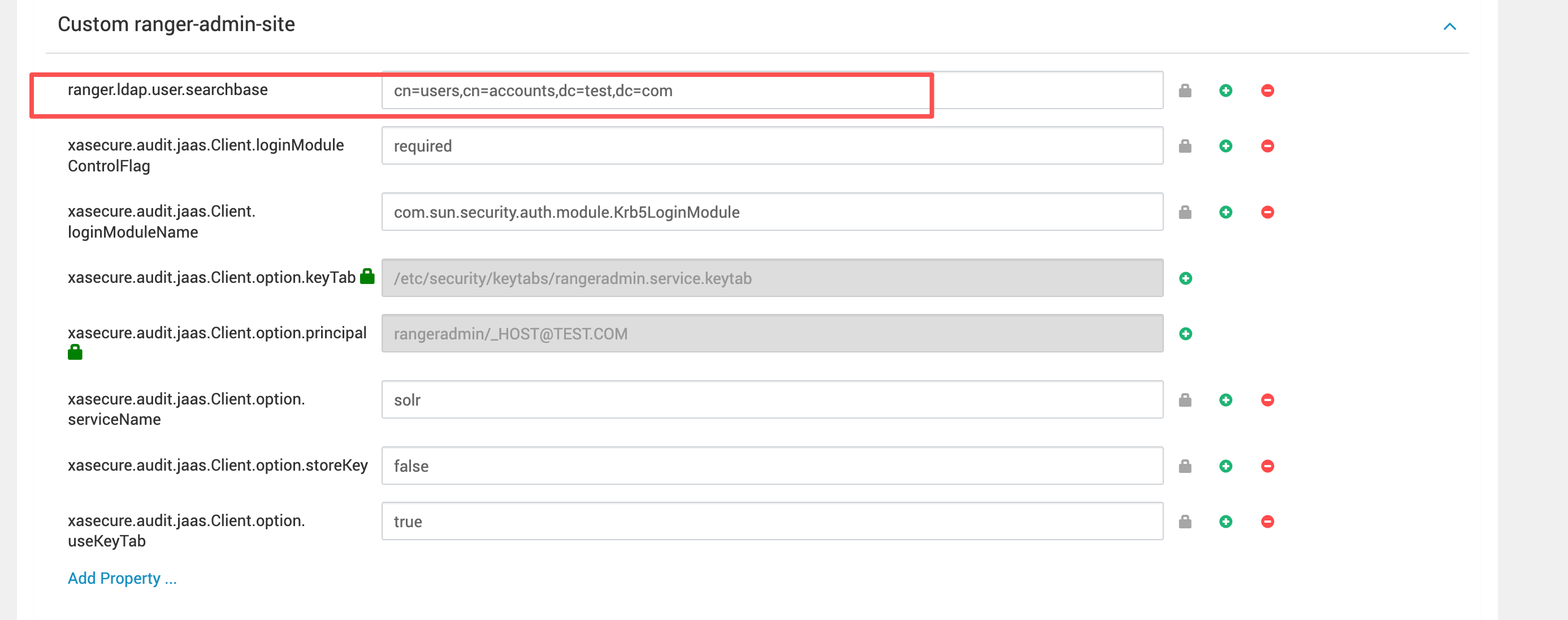
判断是否正确的标准
只要用户真实 DN 在这个 searchBase 之下,就不会出现 No Such Object 这类搜索失败。
一旦 searchBase 写偏,日志里会出现 remaining name 'dc=xxx,dc=yyy'。
# 源码级修复
笔记
修复完后,重启 Ranger admin 服务
- 02
- Ranger Admin 证书快速导入脚本02-15
- 03
- Ranger HBase / Yarn Repository 快速处理02-15
