 [开启Kerberos]-Atlas启动-Kafka权限异常
[开启Kerberos]-Atlas启动-Kafka权限异常
# 一、问题背景
ttr-2.2.1 以上版本已修复
在 ttr-2.2.1 及以上版本中,Atlas 在开启 Kerberos 后已自动适配 Kafka ACL 权限。
若使用早期版本(如 ttr-2.2.0),启动时可能因 Kafka 认证失败 导致 Atlas 无法正常消费 Topic。
如在部署或二开中遇到类似问题,可联系作者 (opens new window) 获取补丁。
Atlas 启动常见的三类权限报错
- HBase 无权限 → 已在前文说明;
- Solr 401 Unauthorized → 已解决;
- Kafka ACL 拒绝访问(本篇重点)。
# 二、问题现象
Atlas 启动后持续报错,日志循环出现如下警告:
2025-11-08 17:06:11,163 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
2025-11-08 17:06:26,123 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:06:41,170 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
2025-11-08 17:06:56,127 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:07:11,173 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
2025-11-08 17:07:26,134 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:07:41,176 [NotificationHookConsumer thread-0] WARN [NetworkClient.java:1100] [Consumer clientId=consumer-atlas-1, groupId=atlas] Error while fetching metadata with correlation id 72 : {ATLAS_HOOK=TOPIC_AUTHORIZATION_FAILED}
2025-11-08 17:07:41,177 [NotificationHookConsumer thread-0] ERROR [Metadata.java:301] [Consumer clientId=consumer-atlas-1, groupId=atlas] Topic authorization failed for topics [ATLAS_HOOK]
2025-11-08 17:07:41,177 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.TopicAuthorizationException: Not authorized to access topics: [ATLAS_HOOK]
2025-11-08 17:07:56,137 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:08:11,178 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
2025-11-08 17:08:26,142 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:08:41,181 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
2025-11-08 17:08:56,146 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:09:11,184 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
2025-11-08 17:09:26,151 [index-health-monitor] INFO [AtlasJanusGraphIndexClient.java:98] indexBackEnd=solr; isHealthy=true
2025-11-08 17:09:41,188 [NotificationHookConsumer thread-0] WARN [NotificationHookConsumer.java:635] Exception in NotificationHookConsumer
org.apache.kafka.common.errors.GroupAuthorizationException: Not authorized to access group: atlas
[root@dev1 atlas]#
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
日志中可见两个关键异常:
| 异常类型 | 说明 |
|---|---|
GroupAuthorizationException | Atlas 无法加入 Kafka 消费组(group=atlas) |
TopicAuthorizationException | Atlas 无权限访问 ATLAS_HOOK 或 ATLAS_ENTITIES Topic |
这表明 Atlas 成功通过 Kerberos 认证,但 Kafka 侧未授予 ACL 访问权限。
# 三、排查与分析
Atlas 通过 NotificationHookConsumer 模块监听 Kafka 的元数据变更事件(ATLAS_HOOK、ATLAS_ENTITIES)。
Kerberos 开启后,Kafka 默认启用 SASL/GSSAPI + ACL 控制,任何主体若未在 ACL 中注册,则拒绝连接。
因此需要为 atlas 用户手动授权。
# 四、修复方案 — 使用 kafka-acls 添加权限
切换到 Kafka 主节点并进入 bin 目录:
cd /usr/bigtop/current/kafka-broker/bin
1
# 1、授权消费组权限(Group)
./kafka-acls.sh \
--authorizer-properties zookeeper.connect=dev1:2181,dev2:2181,dev3:2181 \
--add --allow-principal "User:atlas" \
--group atlas --operation Read --operation Describe --resource-pattern-type LITERAL
1
2
3
4
2
3
4
# 2、授权 Topic 消费权限(ATLAS_HOOK)
./kafka-acls.sh \
--authorizer-properties zookeeper.connect=dev1:2181,dev2:2181,dev3:2181 \
--add --allow-principal "User:atlas" \
--topic ATLAS_HOOK --operation Read --operation Describe --resource-pattern-type LITERAL
1
2
3
4
2
3
4
# 3、授权 Topic 写入权限(ATLAS_ENTITIES)
./kafka-acls.sh \
--authorizer-properties zookeeper.connect=dev1:2181,dev2:2181,dev3:2181 \
--add --allow-principal "User:atlas" \
--topic ATLAS_ENTITIES --operation Write --operation Describe --resource-pattern-type LITERAL
1
2
3
4
2
3
4
# 五、执行结果验证
执行后返回如下输出,说明权限添加成功:
Adding ACLs for resource `ResourcePattern(resourceType=GROUP, name=atlas, patternType=LITERAL)`:
(principal=User:atlas, host=*, operation=DESCRIBE, permissionType=ALLOW)
(principal=User:atlas, host=*, operation=READ, permissionType=ALLOW)
Current ACLs for resource `ResourcePattern(resourceType=GROUP, name=atlas, patternType=LITERAL)`:
(principal=User:atlas, host=*, operation=DESCRIBE, permissionType=ALLOW)
(principal=User:atlas, host=*, operation=READ, permissionType=ALLOW)
1
2
3
4
5
6
7
2
3
4
5
6
7
Topic 授权输出类似:
Current ACLs for resource `ResourcePattern(resourceType=TOPIC, name=ATLAS_HOOK, patternType=LITERAL)`:
(principal=User:atlas, host=*, operation=DESCRIBE, permissionType=ALLOW)
(principal=User:atlas, host=*, operation=READ, permissionType=ALLOW)
Current ACLs for resource `ResourcePattern(resourceType=TOPIC, name=ATLAS_ENTITIES, patternType=LITERAL)`:
(principal=User:atlas, host=*, operation=WRITE, permissionType=ALLOW)
(principal=User:atlas, host=*, operation=DESCRIBE, permissionType=ALLOW)
1
2
3
4
5
6
7
2
3
4
5
6
7
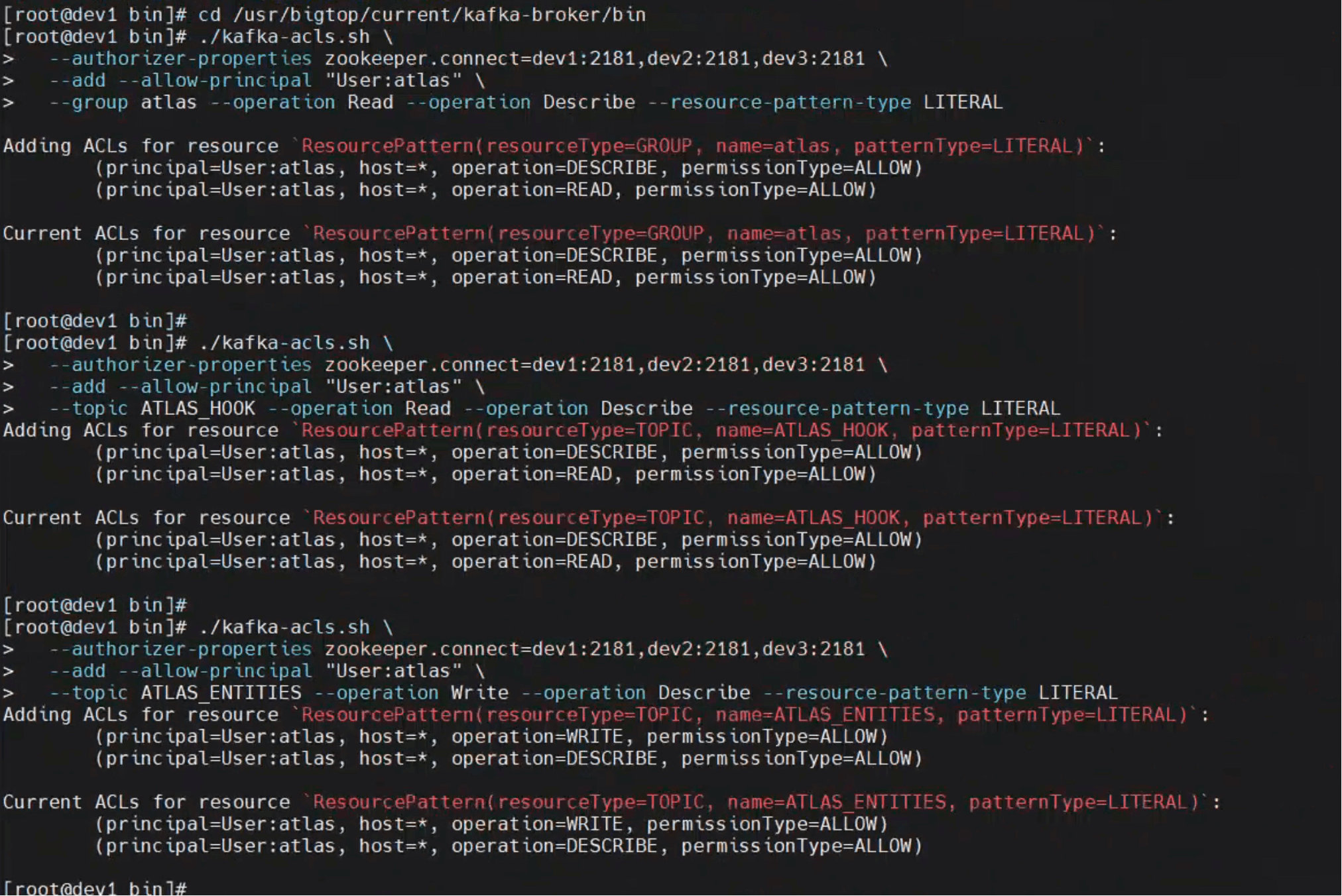
验证成功标志
返回的 “Current ACLs for resource ...” 表示授权已生效,atlas 用户具备读写描述权限。
- 01
- [Step2] Ranger Admin HA 自动化安装 自生成凭证02-04
- 02
- 调用 Ranger API 返回 403 问题02-03
- 03
- [Step1] Haproxy 规划与环境安装 Kylin V1002-02
