 [关闭 Kerberos]-Kafka 注销异常
[关闭 Kerberos]-Kafka 注销异常
# 一、问题背景
在 Ambari 中关闭 Kerberos 时,Kafka 会自动执行以下流程:
zookeeper-security-migration.sh --zookeeper.acl=unsecure
1
2
3
2
3
该脚本的作用是将 Kafka 在 Zookeeper 中的 ACL 从 secure 模式恢复为 unsecure 模式。
但在 BIGTOP 3.2.0(Ambari 3.x)默认实现中存在缺陷,导致关闭 Kerberos 过程中 Kafka 安全迁移失败。
# 二、版本提示(重要)
ttr-2.2.1 及以上版本已修复
从 ttr-2.2.1 开始,此问题已被彻底修复。
在新版本中,Ambari 会正确注入 JAAS 配置,Kafka 能正常访问 Zookeeper 并完成 ACL 回滚。
如你使用 ttr-2.2.0 或更早版本,请参考本篇手动修复。如在部署或二开中遇到类似问题,可联系作者 (opens new window)
获取补丁。
# 三、异常现场:Zookeeper Security Migration 执行失败
关闭 Kerberos 时,Ambari 执行 Kafka 安全迁移脚本并报错:
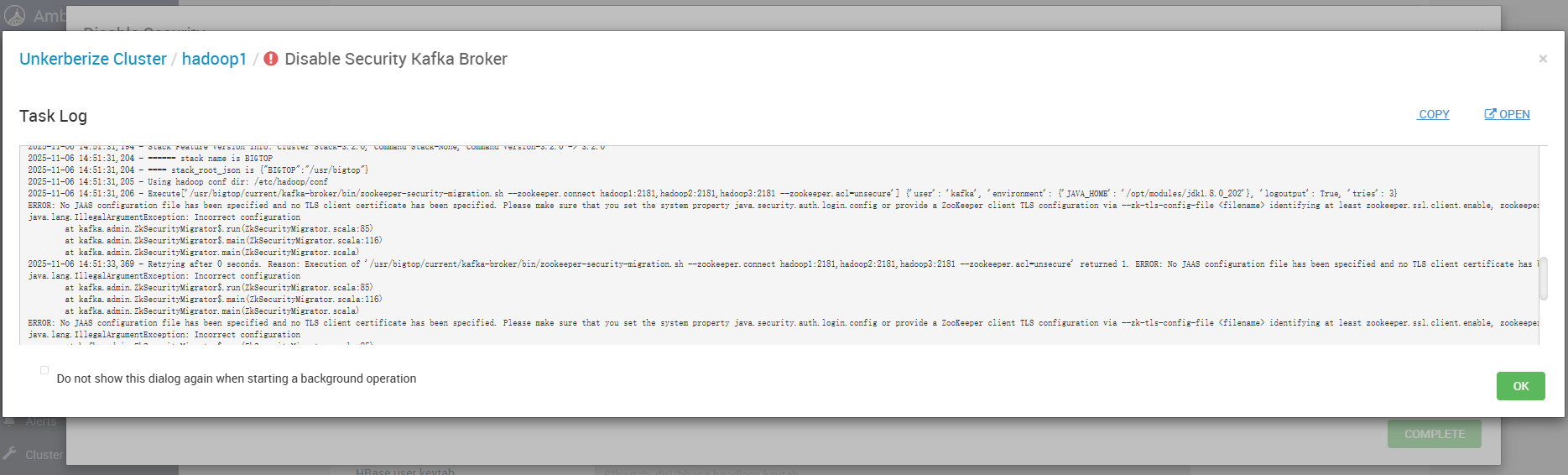
脚本报错内容如下:
stderr:
NoneType: None
The above exception was the cause of the following exception:
Traceback (most recent call last):
File "/var/lib/ambari-agent/cache/stacks/BIGTOP/3.2.0/services/KAFKA/package/scripts/kafka_broker.py", line 173, in <module>
KafkaBroker().execute()
File "/usr/lib/ambari-agent/lib/resource_management/libraries/script/script.py", line 413, in execute
method(env)
File "/var/lib/ambari-agent/cache/stacks/BIGTOP/3.2.0/services/KAFKA/package/scripts/kafka_broker.py", line 152, in disable_security
tries=3)
File "/usr/lib/ambari-agent/lib/resource_management/core/base.py", line 168, in __init__
self.env.run()
File "/usr/lib/ambari-agent/lib/resource_management/core/environment.py", line 171, in run
self.run_action(resource, action)
File "/usr/lib/ambari-agent/lib/resource_management/core/environment.py", line 137, in run_action
provider_action()
File "/usr/lib/ambari-agent/lib/resource_management/core/providers/system.py", line 350, in action_run
returns=self.resource.returns,
File "/usr/lib/ambari-agent/lib/resource_management/core/shell.py", line 95, in inner
result = function(command, **kwargs)
File "/usr/lib/ambari-agent/lib/resource_management/core/shell.py", line 161, in checked_call
returns=returns,
File "/usr/lib/ambari-agent/lib/resource_management/core/shell.py", line 278, in _call_wrapper
result = _call(command, **kwargs_copy)
File "/usr/lib/ambari-agent/lib/resource_management/core/shell.py", line 493, in _call
raise ExecutionFailed(err_msg, code, out, err)
resource_management.core.exceptions.ExecutionFailed: Execution of '/usr/bigtop/current/kafka-broker/bin/zookeeper-security-migration.sh --zookeeper.connect hadoop1:2181,hadoop2:2181,hadoop3:2181 --zookeeper.acl=unsecure' returned 1. ERROR: No JAAS configuration file has been specified and no TLS client certificate has been specified. Please make sure that you set the system property java.security.auth.login.config or provide a ZooKeeper client TLS configuration via --zk-tls-config-file <filename> identifying at least zookeeper.ssl.client.enable, zookeeper.clientCnxnSocket, and zookeeper.ssl.keystore.location
java.lang.IllegalArgumentException: Incorrect configuration
at kafka.admin.ZkSecurityMigrator$.run(ZkSecurityMigrator.scala:85)
at kafka.admin.ZkSecurityMigrator$.main(ZkSecurityMigrator.scala:116)
at kafka.admin.ZkSecurityMigrator.main(ZkSecurityMigrator.scala)
stdout:
2025-11-06 14:51:31,193 - ====== stack name is BIGTOP
2025-11-06 14:51:31,194 - ==== stack_root_json is {"BIGTOP":"/usr/bigtop"}
2025-11-06 14:51:31,194 - Stack Feature Version Info: Cluster Stack=3.2.0, Command Stack=None, Command Version=3.2.0 -> 3.2.0
2025-11-06 14:51:31,204 - ====== stack name is BIGTOP
2025-11-06 14:51:31,204 - ==== stack_root_json is {"BIGTOP":"/usr/bigtop"}
2025-11-06 14:51:31,205 - Using hadoop conf dir: /etc/hadoop/conf
2025-11-06 14:51:31,206 - Execute['/usr/bigtop/current/kafka-broker/bin/zookeeper-security-migration.sh --zookeeper.connect hadoop1:2181,hadoop2:2181,hadoop3:2181 --zookeeper.acl=unsecure'] {'user': 'kafka', 'environment': {'JAVA_HOME': '/opt/modules/jdk1.8.0_202'}, 'logoutput': True, 'tries': 3}
ERROR: No JAAS configuration file has been specified and no TLS client certificate has been specified. Please make sure that you set the system property java.security.auth.login.config or provide a ZooKeeper client TLS configuration via --zk-tls-config-file <filename> identifying at least zookeeper.ssl.client.enable, zookeeper.clientCnxnSocket, and zookeeper.ssl.keystore.location
java.lang.IllegalArgumentException: Incorrect configuration
at kafka.admin.ZkSecurityMigrator$.run(ZkSecurityMigrator.scala:85)
at kafka.admin.ZkSecurityMigrator$.main(ZkSecurityMigrator.scala:116)
at kafka.admin.ZkSecurityMigrator.main(ZkSecurityMigrator.scala)
2025-11-06 14:51:33,369 - Retrying after 0 seconds. Reason: Execution of '/usr/bigtop/current/kafka-broker/bin/zookeeper-security-migration.sh --zookeeper.connect hadoop1:2181,hadoop2:2181,hadoop3:2181 --zookeeper.acl=unsecure' returned 1. ERROR: No JAAS configuration file has been specified and no TLS client certificate has been specified. Please make sure that you set the system property java.security.auth.login.config or provide a ZooKeeper client TLS configuration via --zk-tls-config-file <filename> identifying at least zookeeper.ssl.client.enable, zookeeper.clientCnxnSocket, and zookeeper.ssl.keystore.location
java.lang.IllegalArgumentException: Incorrect configuration
at kafka.admin.ZkSecurityMigrator$.run(ZkSecurityMigrator.scala:85)
at kafka.admin.ZkSecurityMigrator$.main(ZkSecurityMigrator.scala:116)
at kafka.admin.ZkSecurityMigrator.main(ZkSecurityMigrator.scala)
ERROR: No JAAS configuration file has been specified and no TLS client certificate has been specified. Please make sure that you set the system property java.security.auth.login.config or provide a ZooKeeper client TLS configuration via --zk-tls-config-file <filename> identifying at least zookeeper.ssl.client.enable, zookeeper.clientCnxnSocket, and zookeeper.ssl.keystore.location
java.lang.IllegalArgumentException: Incorrect configuration
at kafka.admin.ZkSecurityMigrator$.run(ZkSecurityMigrator.scala:85)
at kafka.admin.ZkSecurityMigrator$.main(ZkSecurityMigrator.scala:116)
at kafka.admin.ZkSecurityMigrator.main(ZkSecurityMigrator.scala)
2025-11-06 14:51:35,436 - Retrying after 0 seconds. Reason: Execution of '/usr/bigtop/current/kafka-broker/bin/zookeeper-security-migration.sh --zookeeper.connect hadoop1:2181,hadoop2:2181,hadoop3:2181 --zookeeper.acl=unsecure' returned 1. ERROR: No JAAS configuration file has been specified and no TLS client certificate has been specified. Please make sure that you set the system property java.security.auth.login.config or provide a ZooKeeper client TLS configuration via --zk-tls-config-file <filename> identifying at least zookeeper.ssl.client.enable, zookeeper.clientCnxnSocket, and zookeeper.ssl.keystore.location
java.lang.IllegalArgumentException: Incorrect configuration
at kafka.admin.ZkSecurityMigrator$.run(ZkSecurityMigrator.scala:85)
at kafka.admin.ZkSecurityMigrator$.main(ZkSecurityMigrator.scala:116)
at kafka.admin.ZkSecurityMigrator.main(ZkSecurityMigrator.scala)
ERROR: No JAAS configuration file has been specified and no TLS client certificate has been specified. Please make sure that you set the system property java.security.auth.login.config or provide a ZooKeeper client TLS configuration via --zk-tls-config-file <filename> identifying at least zookeeper.ssl.client.enable, zookeeper.clientCnxnSocket, and zookeeper.ssl.keystore.location
java.lang.IllegalArgumentException: Incorrect configuration
at kafka.admin.ZkSecurityMigrator$.run(ZkSecurityMigrator.scala:85)
at kafka.admin.ZkSecurityMigrator$.main(ZkSecurityMigrator.scala:116)
at kafka.admin.ZkSecurityMigrator.main(ZkSecurityMigrator.scala)
Command failed after 1 tries
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
核心问题即:
Ambari 执行该脚本时没有加载 kafka_jaas.conf,因此 Kafka 客户端无法进行 Kerberos 认证。
# 四、原因分析:Ambari 未传入 KAFKA_OPTS
问题源于 Ambari 的脚本:
services/KAFKA/package/scripts/kafka_broker.py
1
其中 disable_security 执行迁移脚本时 未附带 JVM 参数:
-Djava.security.auth.login.config=/etc/kafka/conf/kafka_jaas.conf
1
导致 Kafka 以“无认证”模式访问 Zookeeper,自然无法修改 ACL。
# 五、解决方案:显式注入 JAAS 配置
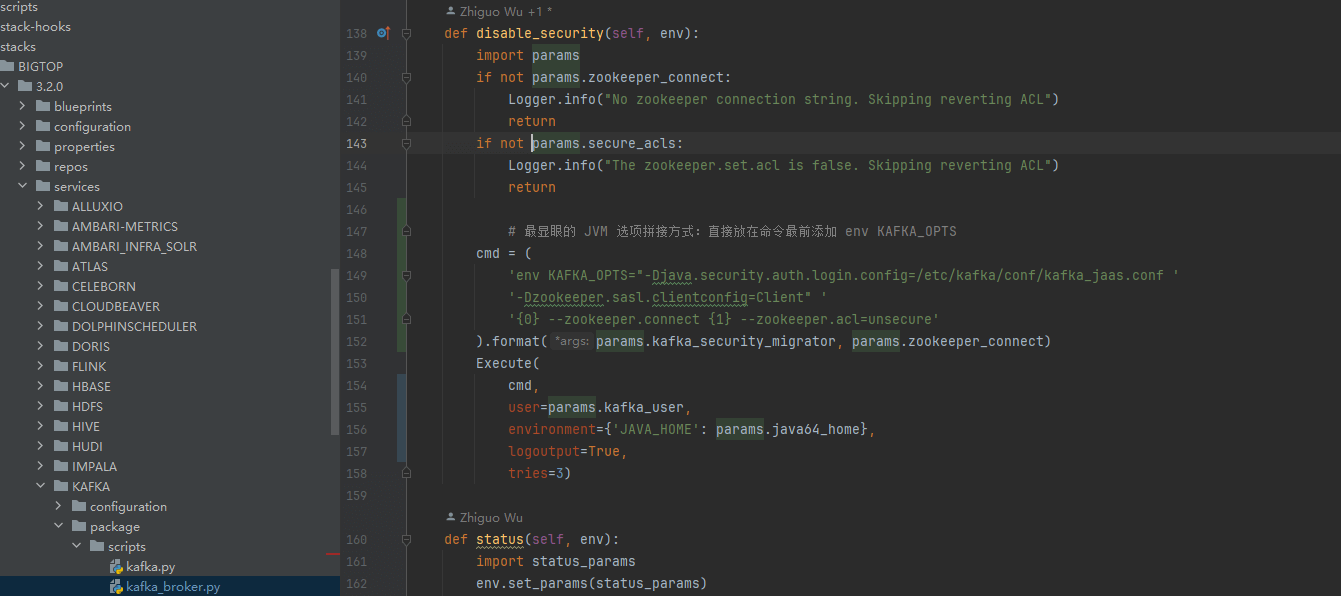
# 1、修改 kafka_broker.py
加入 KAFKA_OPTS,让迁移脚本能正确加载 JAAS:
def disable_security(self, env):
import params
if not params.zookeeper_connect:
Logger.info("No zookeeper connection string. Skipping reverting ACL")
return
if not params.secure_acls:
Logger.info("The zookeeper.set.acl is false. Skipping reverting ACL")
return
cmd = (
'env KAFKA_OPTS="-Djava.security.auth.login.config=/etc/kafka/conf/kafka_jaas.conf '
'-Dzookeeper.sasl.clientconfig=Client" '
'{0} --zookeeper.connect {1} --zookeeper.acl=unsecure'
).format(params.kafka_security_migrator, params.zookeeper_connect)
Execute(
cmd,
user=params.kafka_user,
environment={'JAVA_HOME': params.java64_home},
logoutput=True,
tries=3
)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# 2、Ambari 有两套脚本,需要全部替换
/var/lib/ambari-server/resources/stacks/BIGTOP/3.2.0/services/KAFKA/package/scripts/kafka_broker.py
/var/lib/ambari-agent/cache/stacks/BIGTOP/3.2.0/services/KAFKA/package/scripts/kafka_broker.py
1
2
2
如不替换 agent 侧,执行时仍然会调用旧版本。
# 六、替换后成功执行效果(完整截图)
修改后再次关闭 Kerberos,可看到迁移脚本能够正确运行。
成功日志:

最终日志输出:
stderr:
None
stdout:
2025-11-06 15:46:07,433 - ====== stack name is BIGTOP
2025-11-06 15:46:07,433 - ==== stack_root_json is {"BIGTOP":"/usr/bigtop"}
2025-11-06 15:46:07,434 - Stack Feature Version Info: Cluster Stack=3.2.0, Command Stack=None, Command Version=3.2.0 -> 3.2.0
2025-11-06 15:46:07,450 - ====== stack name is BIGTOP
2025-11-06 15:46:07,450 - ==== stack_root_json is {"BIGTOP":"/usr/bigtop"}
2025-11-06 15:46:07,453 - Using hadoop conf dir: /etc/hadoop/conf
2025-11-06 15:46:07,454 - Execute['env KAFKA_OPTS="-Djava.security.auth.login.config=/etc/kafka/conf/kafka_jaas.conf -Dzookeeper.sasl.clientconfig=Client" /usr/bigtop/current/kafka-broker/bin/zookeeper-security-migration.sh --zookeeper.connect hadoop1:2181,hadoop2:2181,hadoop3:2181 --zookeeper.acl=unsecure'] {'user': 'kafka', 'environment': {'JAVA_HOME': '/opt/modules/jdk1.8.0_202'}, 'logoutput': True, 'tries': 3}
Warning: The following secure root paths do not exist in ZooKeeper: /controller
That might be due to an incorrect chroot is specified when executing the command.
[2025-11-06 15:46:10,144] WARN TGT renewal thread has been interrupted and will exit. (org.apache.zookeeper.Login)
Command completed successfully!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Kafka 安全回滚顺利完成,关闭 Kerberos 继续执行下一阶段。
- 01
- [Step2] Ranger Admin HA 自动化安装 自生成凭证02-04
- 02
- 调用 Ranger API 返回 403 问题02-03
- 03
- [Step1] Haproxy 规划与环境安装 Kylin V1002-02
